i am reading lately a lot about hash from torrents an magnetic links etc.
- How To Download Torrent Using Hash File
- How To Download Torrent Using Hash On Pc
- Download Torrent With Hash
- Utorrent
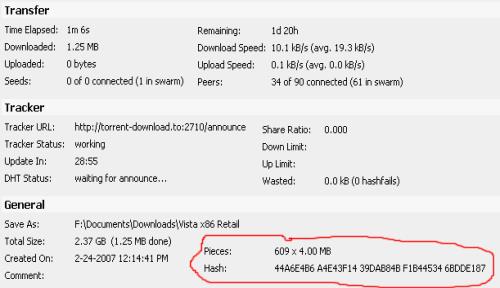
but there is a question i dont understand.
- The Pirate Bay has removed torrent file links of the torrents being shared by more than 10 people. However, there are a few ways to download the actual torrent links instead of magnet links. How to download the.torrent files. Using the hash value of the torrent file: Each torrent file on The Pirate Bay comes with a hash value.
- Info hash: (mandatory) torrent name: (this is not an URL, this is a string you will see in the client) Magnet Link.
I have the hash of a file and the infohash of a torrent, is the infohash = hash of the file ?
If yes what if the torrent descripes 6 Files to download ?
Since you’re probably using torrents to download movies in most cases anyway, there’s actually no need for you to download the whole file on your computer or mobile device. Just add the torrent to the Downloaded, let myfastfile download it for you and simply stream the whole thing without downloading it and needing to wait! Jun 14, 2016 - you must need trackers for a torrent to be downloaded in magnet link here is an api which gives you current seeders and leechers include with.
If no what does it stand for.
1 Answer
So I finally figured it out.
The “infohash” is the SHA1 Hash over the part of a torrent file that includes:
- ITEM: length(size) and path (path with filename)
- Name: The name to search for
- Piece length: The length(size) of a single piece
- Pieces: SHA1 Hash of EVERY piece of this torrent
- Private: flag for restricted access
To show this a little more I took a random torrent file and used the “BEncode Editor” from Ultima to make it more clearly to me.
As you can see the the red box marked the information part of the torrent file.The torrent file includes not the Hash of the items, but the hashes of every piece.
- For item1 with: 1069496548
- and item2 with: 223
- It is together: 1069496771
- With a piece size of: 524288
- There are 2040 pieces. (1069496771/524288=2039.9032 approximately)
- The pieces section includes 40800 byte of data what are 81600 + 2 chars in the file.
- the +2 because 0x marks that this is hexadecimal.
- A SHA1 hash has 40 0x chars or 20 Byte of data what are 2040 SHA1 hashes.
I am sorry that this information is about a torrent that leads to a illegal movie, but i wanted to use a torrent that realy exists.
Not the answer you're looking for? Browse other questions tagged hashtorrentinfo-hash or ask your own question.
I know we use hash functions to check for the integrity of the files etc... but my question is how can we check for the integrity of the files being downloaded from some server?
2 Answers
Integrity is defined only relatively to an authoritative source which tells what the 'correct' sequence of byte is. Hash functions don't create integrity, they transport it. Basically, if you have:
- a file;
- a hash value, presumed correct;
then you can recompute the hash function over the file and see if you get the same hash value.
You still have to start somewhere. Some software distributors provide, along with the software, a 'checksum' (or 'md5sum' or 'sha1sum') file, which contains the hash values. Assuming you got the correct checksum file, this allows you to verify whether you downloaded the right file, down to the last bit; and this works regardless of how you downloaded the possibly big file (even if it came over some shady peer-to-peer network or whatever; you cannot cheat hash functions).
Now this does not solve the integrity problem; it just reduces it to the problem of making sure that you got the right hash value. Hash values are small (32 bytes for SHA-256) so this opens a lot of possibilities. In the context of downloading files from P2P systems, you could obtain the hash value from a HTTPS Web site (HTTPS uses SSL which ensures server authentication -- you have the guarantee that you talk to the server you intend -- and transport integrity -- what you receive is guaranteed to be what the server sent). In the context of exchanging PGP public keys with people, hash values (often called 'fingerprints' or 'thumbprints') are short enough to be transferred manually (printed on a business card, spelled over phone...).
How To Download Torrent Using Hash File
Digital signatures expand on the concept, but they too begin with hash functions. All digital signature algorithms sign not the message itself, but the hash of the message (which is equally good as long as the hash function is secure, i.e. resistant to collisions and preimages).
For many pieces of software, the providers of the files also provide the hash of the file that allows you to verify it's integrity.
How To Download Torrent Using Hash On Pc
For example, here is an example of the checksums the Fedora Project provides for the Fedora 19 x86_64 ISO.
Download Torrent With Hash
Instructions are also provided as well if one does not how to use the provided checksums.
Generally, if the files are provided through the same medium as the checksums, there is very little real benefit as an attacker that manages to compromise the download will also have the capability to replace the provided checksum. However, this is very useful in the case of the files being downloaded over an insecure connection like torrents or a CDN. In such a situation, the software provider can provided the small checksum on his server while serving the files through a higher bandwidth medium such as torrents or a CDN.



